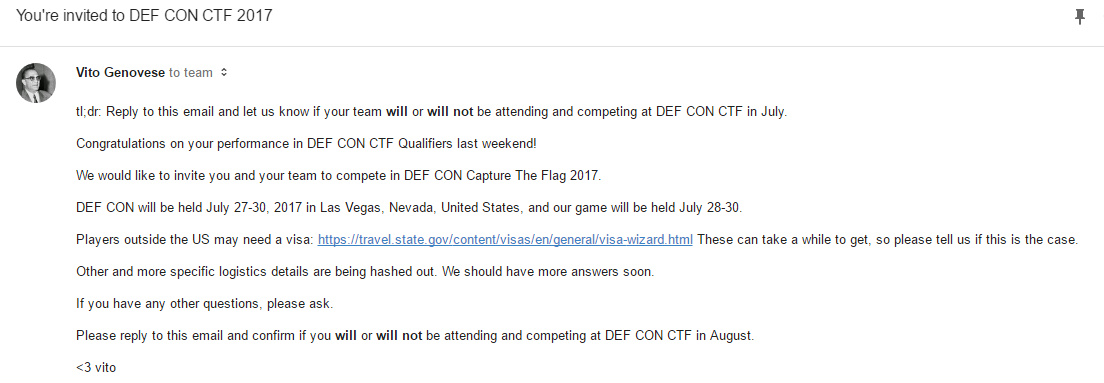
Update 5/5/17: We qualified to DEF CON CTF 2017!!! We just got the email today! Congrats to everyone from Lab RATs, TechSec, and RPISEC that competed. Vegas, here we come!
This past weekend, I competed in my first DEF CON CTF Qualifier. Our club TechSec teamed up with Lab RATs (Lincoln Labs’ CTF team) and RPISEC, and this powerhouse team ended up placing 10th. We beat out some very strong teams, including LCBC (the top Russian team), Dragon Sector (Poland), KaisHack (Korea Advanced Inst. of Science and Tech), and binja (Japan).
What’s at stake
Held in Las Vegas every July at the DEF CON conference, DEF CON CTF attracts the best hacking teams in the world. Teams compete year-round to nab a qualification spot in Vegas and have a chance at the title.
Format and griping
Let me get a few complaints out of the way. A few things that bother me about DEF CON CTF are the lack of clarity on qualification rules and the frustrating format of the qualifier. First of all, all the challenges are Reverse Engineering and Pwn/Exploitation — most are totally inaccessible to beginners like most of TechSec’s members. There was one problem in the Web category that actually turned out to be pwn as well (surprise!). Also, for the first two days, only a few challenges are ever available at a time, because most are locked. The team that solves the most recent challenge gets to choose which challenge to unlock next. The small numbers of challenges are meant to not overwhelm smaller teams — but on the last day, the floodgates open…
LegitBS has been organizer of the CTF since 2013. They usually take 15 teams from eight prequalifying events + DEF CON Quals, but how they deal with teams that qualify multiple times is uncertain. I wish they were more clear/communicative about this.
Last year, LegitBS took ten from DEF CON Quals because two teams (LCBC and PPP) prequaled twice and another prequaled team (StratumAuhuur) dropped out. This year, it seems that they’re taking nine, just missing us 😦. At the very least, we helped Lab RATs jump from 32nd place to 10th from last year to this year. We will probably receive an email later this week as to whether we’ve qualified or are first alternates. There’s a small chance we may still make it, if another team drops out or a team that’s already qualed wins the last qualifying event, 0ctf, in June.
Regardless of whether we end up qualifying, I had a thrilling experience. Rahul (fortenforge) and I worked with Lincoln at the BeaverWorks space the whole weekend, contributing where we could. We took the occasional break for Lego Batman, MIT tent parties, and sleep, but otherwise we were plugged in.
In the antepenultimate hour, our team solved three challenges in quick succession — awsno (the web chal), pegem, and pepperidge farm. That put us in a tie with two other teams, and we needed just one more solve to guarantee our spot. We were working on four other chals, none of which we ended up solving in time.
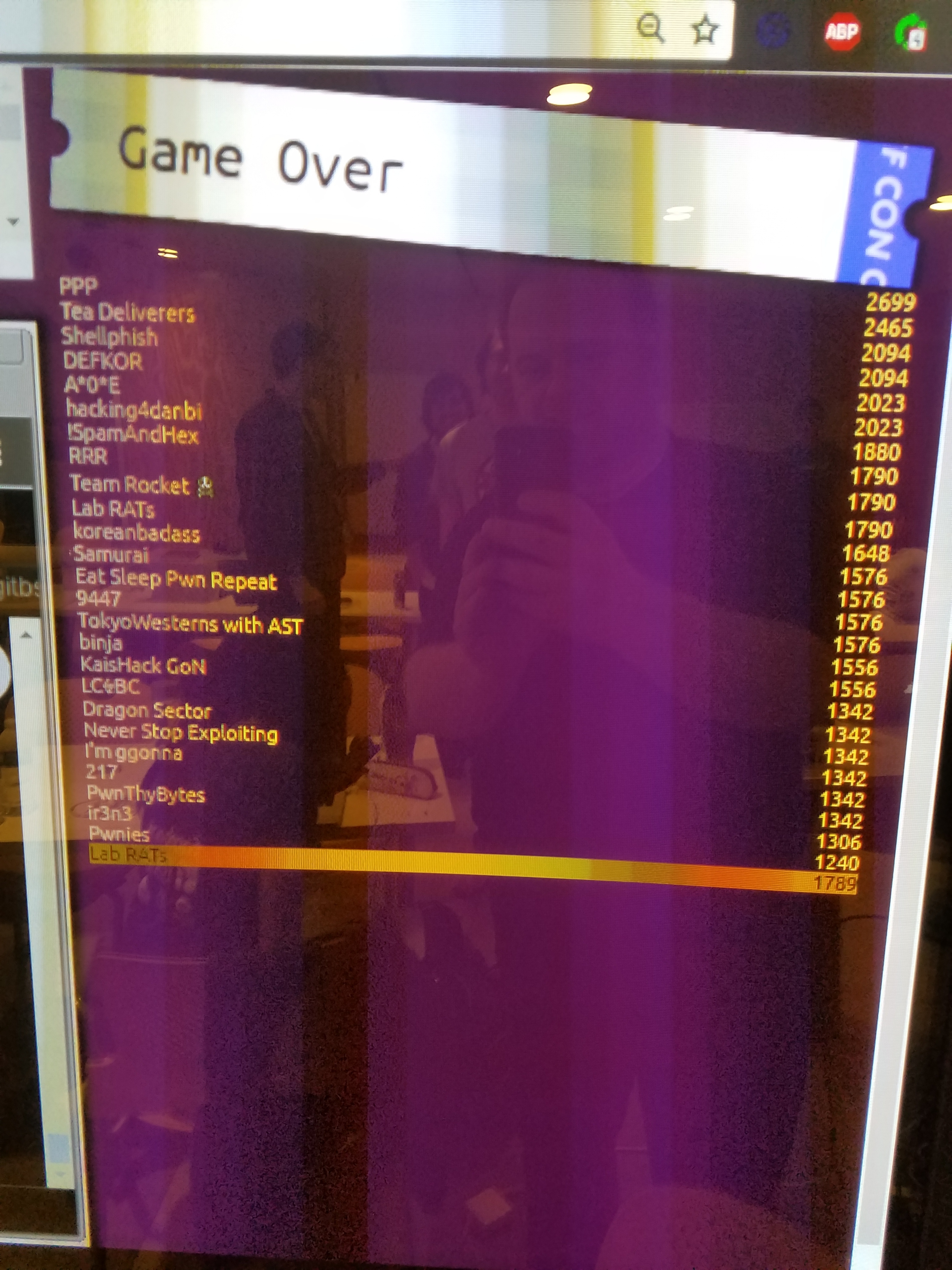
Challenges
I won’t be doing full writeups in this blog post, but I’ll be describing some of my favorite challenges briefly.
Pegem
Pegem was a problem in the RE category (but actually pwn) in the one-instruction esolang SUBLEQ (SUbtract and Branch if Less than or EQual to zero). You had to solve a peg game written in SUBLEQ, run by a C emulator. Once you won the game, there was a “buffer overflow” that allowed you to modify the SUBLEQ program itself, changing its control flow to print out the flag byte-by-byte.
The flag: Who needs more than one instruction?
Insanity!!!
This challenge took in audio files zlib-compressed, and used a speech-to-text library to interpret each word as either ‘insanity’ or ‘insane’. Depending on how many ‘insanities’ were preceding an ‘insane’, the program would execute one of 9 opcodes in a stack-based interpreter. The exploitable bugs were in the interpreter, so we used OSX’s say command to produce audio files with the word insanity repeated 1-100 times. Thanks Samantha (or Siri, as you might know her)!
Jargon
vito fuzyll + gynophage hj hoju = bja lightning fuzyll
That’s the kind of shit that I spent the wee hours of Sunday staring at. This was a black-box RE problem that took in nibbles of data over a network port, and interpreted them as random words or names of the organizers — vito, selir, jymbolia, etc. Each nibble corresponded to an opcode for a stack-based interpeter — dead beaf was push, xyzzy was multiply. I discovered a syscall opcode that took whatever was pushed onto the stack and executed that syscall, so I started fuzzing until I found one valid syscall — hj hoju, that pushed a bunch of crap to the stack. This crap turned out to be the flag, once fortenforge figured out how the words corresponded to digits! Quite a team effort and a fun problem, though I wish we had solved a bit faster, given that I was staring at the flag without realizing it for hours.
All we can do now is wait and see… at the very least, our chances look good for next year.